How to secure my crypto wallet in 2025
How to get started with the safest crypto wallet
- Download the Best Wallet app directly to your iOS or Android mobile device.
- Configure all the top-tier security measures, such as biometric and 2FA logins.
- Buy, receive, swap, and manage your crypto holdings all within the Best Wallet app.
How to secure your crypto wallet
The following safety tips should be followed when exploring the question: How to secure my crypto wallet?
Set up 2FA
The first step is to ensure 2FA is set up and activated. This feature can be found in the “Settings” tab in the Best Wallet app.
So, why is 2FA important? Put simply, 2FA adds an extra layer of security before accessing the wallet funds. With Best Wallet, users initially provide a mobile number. A verification code is sent via SMS, which must be entered to provide ownership. This step is repeated whenever the Best Wallet app is opened.
This ensures unauthorized access isn’t possible, even if the wallet is hacked remotely. For instance, suppose the user mistakenly engages with a malicious smart contract, which instructs the wallet balance to be transferred to the hacker. However, the funds can’t be transferred unless the 2FA step is completed.
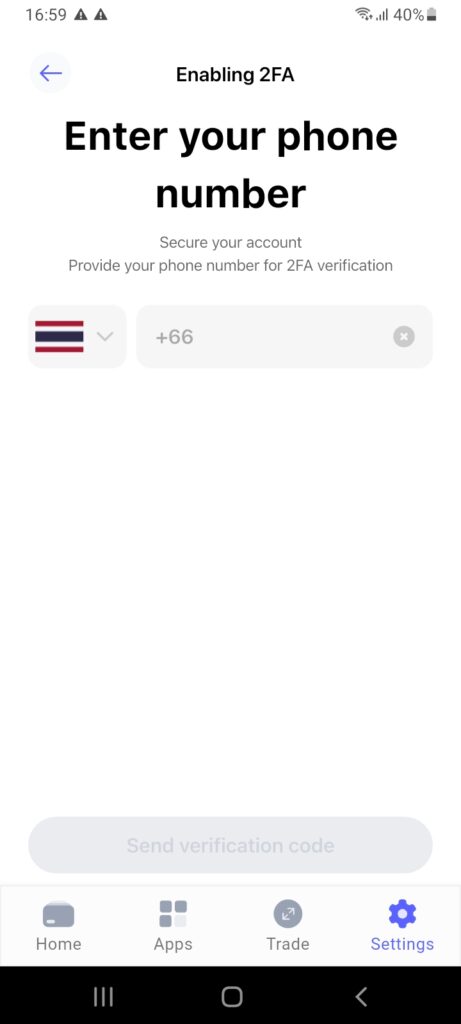
This means entering the unique SMS code that’s sent to the registered number. The hacker wouldn’t be able to obtain the code, considering they don’t have access to the device. 2FA is even stronger when using a secondary device specifically for security.
For instance:
- The primary device could be used to manage the Best Wallet app, including sending, receiving, and trading cryptocurrencies.
- The secondary device could be used for receiving the 2FA code.
Hackers or even real-world criminals would require both devices to stand any chance of accessing the wallet balance. However, just remember that 2FA is an optional security measure, considering some users don’t feel comfortable providing their mobile numbers. However, Best Wallet strongly advises that it be activated.
Use biometric login options
Biometrics should also be considered when exploring how to secure my crypto wallet. In a nutshell, biometrics are unique physical traits that are unique to the user. This can include anything from facial recognition to voice and retina scans. Fingerprint ID is also a popular biometric, which is available to Best Wallet users.
According to the National Cyber Security Centre, biometrics are a safer alternative to traditional passwords or PINs. Biometrics can’t be guessed, misplaced, or remotely hacked by cybercriminals. This ensures access to the Best Wallet app is only possible when providing a fingerprint scan.
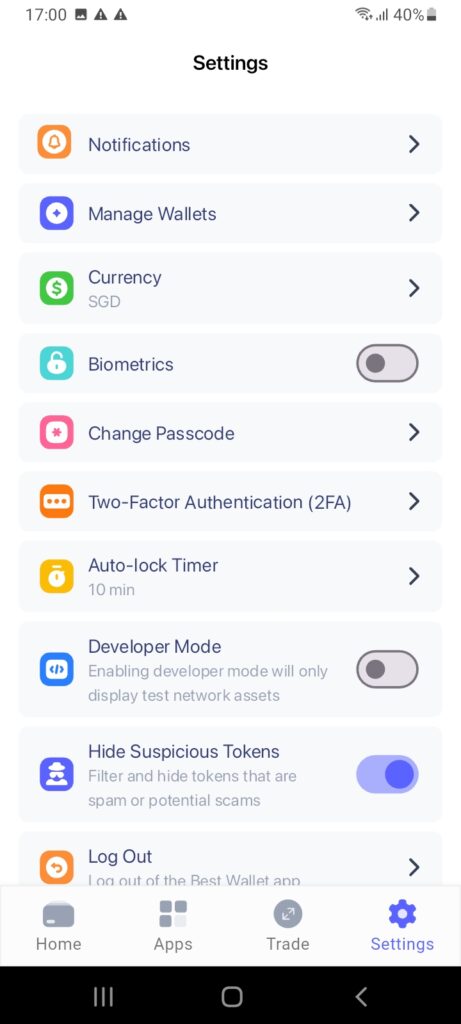
What’s more, the user’s fingerprint ID only works on the respective device that Best Wallet is installed on. This is because the wallet’s private key is encrypted and downloaded on the smartphone, which connects to the Best Wallet app. Therefore, we strongly advise users to activate biometrics straightaway. This can be done via the “Settings” tab.
Use a password manager
While biometrics is the recommended security measure, some crypto users prefer traditional passwords. In this regard, password managers should always be used. These are software applications (mobile or desktop) that provide the following core functions:
Password generation
First, password managers ensure that highly complex passwords are generated. These will contain a mixture of upper and lower case letters, numbers, and special characters (e.g. ! or $). This ensures that users don’t create passwords that are too short or easy to guess.
Crucially, it’s virtually impossible for hackers to “crack” long and complex passwords, considering the sheer amount of computational power required. So, instead of using something like “Password123”, you’d benefit from a password like “aXmnZK276rf*&DaaE”.
Password encryption
Password managers also ensure that generated passwords are encrypted. This means hackers cannot view the saved passwords even if remote access is gained.
Password storage
Users can easily obtain their generated passwords when using password managers. It’s just a case of copying and pasting the password from the software application. This ensures the generated long and complex passwords aren’t cumbersome to manage.
Ultimately, using a password manager is highly recommended when exploring the question: How to secure a crypto wallet?
Don’t use your wallet on public WiFi networks
The next best practice is to avoid using a crypto wallet on public WiFi networks. While convenient, public WiFi is often unsecured, making it attractive to hackers, especially when deploying the “man-in-the-middle” attack. Falling victim to this cybercrime method can be highly detrimental to your wallet balance.
For instance, suppose you connect to an unsecured WiFi network in a coffee shop. The hacker could intercept the connection on the same network, meaning they can potentially access everything on the device. Without proper security controls (e.g., biometrics and 2FA), the wallet funds could be drained in seconds.
Therefore, Best Wallet strongly suggests keeping wallet usage to privately owned WiFi networks. If access is required when in public, use the smartphone’s 4/5G data service. Adding a virtual private network (VPN) adds an extra layer of security. Many VPN providers offer a free service, so consider this an added security measure.
Keep your crypto holdings private
Keeping digital asset holdings private is crucial when exploring the question: How to secure my crypto wallet? After all, hackers will directly target people they know have significant crypto investments. As a safety precaution, users are strongly advised to avoid posting about crypto-related holdings on social media.
Privacy should also extend to people in the real world. There are increasing cases of crypto investors being kidnapped, with criminals forcing victims to reveal their wallet credentials before stealing the funds. Unlike traditional investments like stocks or ETFs, most crypto thefts are unrecoverable, considering the anonymous nature of digital assets.
Beware of phishing emails and scams
Phishing is another major risk in the Bitcoin space. Therefore, phishing methods should be understood fully when exploring how to make your crypto secure. In simple terms, phishing attacks aim to trick users into thinking they’ve received an email or telephone call from a legitimate company.
- For example, suppose you’re storing cryptocurrencies in the Best Wallet app.
- You receive an email from a scammer claiming to be from the Best Wallet security team.
- The scammer claims that your wallet balance is at risk and requests you send them your backup passphrase.
- If you do so, the hacker can access your wallet balance remotely, even without the 2FA code or biometrics.
- The wallet balance would be stolen immediately, with no means to recover the funds.
For a start, Best Wallet will never request the user’s credentials, whether that’s backup passphrases, private keys, or personal information. On the contrary, Best Wallet is a self-custody provider, so has no reason to ever contact users directly.
If, however, you’re using other crypto providers, such as an online exchange, be extra cautious about phishing risks. The best practice is to contact the provider directly from their official communication methods (live chat, telephone, etc.). Ultimately, legitimate companies will never ask for sensitive crypto wallet data.
Check website URLs to avoid fake sites
Scammers frequently create “fake sites” to trick crypto investors. Connecting your wallet to such sites will likely mean its contents are drained. For example, suppose you’re looking to swap cryptocurrencies on Uniswap. However, instead of visiting “Uniswap.org,” you mistakenly visit “Uni-swap.org.”
This means you’re connecting a wallet address to an imitation site rather than the official Uniswap exchange. Thus, hackers will access and steal the wallet funds accordingly. The best practice is to always double-check the URL before proceeding. It’s also wise to bookmark the official website for future use. This will keep your crypto secure.
Keep software updated
Software updates are also crucial when exploring the question of how to secure your Bitcoin wallet. Updates are critical in protecting devices from new vulnerabilities like malware and viruses. Using outdated software can mean the device isn’t adequately protected.
Best Wallet users should ensure that the app and the device’s operating system are regularly updated. This provides broader protection against online hackers. Best Wallet alerts users when a new app update is available—we advise doing so immediately.
Use self-custodial wallets
Non-custodial wallets like Best Wallet ensure users have full control over their crypto funds. Unlike custodial wallets, they don’t rely on a centralized provider. For example, consider an investor who keeps their cryptocurrencies on an exchange. Those cryptocurrencies are at risk of loss if the exchange is hacked.


Exchanges have a single point of failure, so a hack can provide access to all client-owned funds. Bybit, for example, was hacked in February 2025, with over $1.5 billion worth of Ethereum stolen. Custodial wallet providers can also engage in malpractice, such as FTX “misplacing” billions of dollars worth of user funds.
In contrast, self-custody wallets are decentralized. Best Wallet users benefit from an encrypted Bitcoin wallet, ensuring a trustless experience. Only the wallet owner can authorize transactions, so there’s no requirement for approval from a third party. Crypto balances can’t be restricted or frozen either, considering Best Wallet doesn’t have access to the private keys.
Only use wallets without a history of hacking
Reputation is key to ensuring crypto wallet security. Investors should only consider wallet providers with robust safety measures and a solid track record. This means avoiding providers that have previously witnessed a hack.
Best Wallet has never been breached by cybercriminals, which is a testament to our institutional-grade security controls. From biometrics, encrypted private keys, and 2FA, Best Wallet users are safe and protected from malicious actors.
Choosing the most secure crypto wallet
We’ve answered the question extensively: How to secure my crypto wallet? The next step is understanding how to choose a secure wallet provider.
Let’s take a closer look at the key considerations.
Self-custody vs custodial wallets
Wallets can be split into two key categories – “self-custody” and “custodial.” The one you choose determines who controls the private keys.
In a nutshell:
- Self-custody wallets provide full ownership and control. Only the user has access to the private keys, so third parties can’t restrict transactions or freeze wallet balances.
- Users lose control of their crypto funds when using custodial wallets. Private keys are safeguarded by third parties, so users need permission to transact.
Best Wallet offers a self-custody wallet, ensuring nobody but the user can control its contents. This isn’t the case when opting for a custodial wallet, such as an online exchange.
The sections below explain how self-custody and custodial wallets treat private keys, transaction approval, anonymity, and other key factors.
Private Keys and Transaction Approval
The private key dictates who can access a crypto wallet, including authorizing transactions.
- For example, suppose you open an account with a crypto exchange. You buy $2,000 worth of Bitcoin with a credit card.
- The purchased Bitcoins are immediately added to your exchange balance, meaning you’re using a custodial wallet.
- Only the exchange has access to the wallet’s private key, so you require permission to withdraw the funds.
- There are no guarantees that the withdrawal will be approved. The balance could be restricted or the account unjustifiably closed at any time.
- This means the Bitcoins cannot be transferred from the online exchange.
Now consider the same scenario but with a self-custody wallet like Best Wallet. Once Bitcoins are added to the balance, Best Wallet has no control over the funds. Only the user has access to the private key, which is encrypted and stored on the smartphone device.
Put otherwise, users can send, receive, and trade crypto without needing permission. This ensures a secure and decentralized experience.
Centralized Security Risks
Centralized risks should also be assessed when exploring the question: How to secure my crypto wallet?
We’ve established that custodial wallets are offered by centralized platforms, usually online exchanges. These exchanges have a single point of failure. One successful hacking attempt could mean its entire wallet balances are compromised. The result? Client-owned funds will be stolen, with no guarantee the exchange will cover the loss.
In contrast, self-custody wallets like Best Wallet are decentralized. Best Wallet doesn’t touch client-owned cryptocurrencies. Nor does it have access to any private keys. Best Wallet is simply an application that connects users to the blockchain. Therefore, even if Best Wallet’s servers were attacked, this couldn’t directly impact users.
Privacy and Data Breaches
Privacy is another consideration when choosing between self-custody and custodial wallets. In most cases, users must complete traditional know-your-customer (KYC) processes when opting for the latter. This is because custodial wallets are usually offered by centralized exchanges, which must comply with anti-money laundering regulations.
This means providing personal information and verification documents, such as government-issued ID and proof of address (e.g., a recently issued bank statement). Now, not only does this mean crypto investors must reveal their identities, but the uploaded information is at risk. A security breach could mean sensitive documents get into the wrong hands.
As such, the best way to store crypto securely is via a self-custody wallet. Best Wallet users enjoy a private, anonymous experience. Wallets are downloaded and managed without KYC data ever being requested. Not only when sending and receiving cryptocurrencies but also when buying, selling, and trading.
Software vs Hardware Wallets
We’ve now explained the difference between self-custody and custodial wallets. The next wallet category to explore is software and hardware solutions.
In a nutshell:
- Software wallets, including mobile apps, desktop software, and browser extensions. They provide seamless access to the crypto markets. All that’s needed is an internet connection.
- Hardware wallets are physical devices. They store private keys within the device and never connect to the internet. Hardware wallets are best suited to long-term investors storing significant balances.
Choosing between a software and hardware wallet is an important decision. Let’s take a closer look at how they compare.
Software Wallets
Software wallets provide the ideal balance between security and convenience. They’re the best option for active crypto traders, considering software wallets are always internet-ready. For example, suppose you’re using the Best Wallet app. Upon opening the app, biometrics and 2FA steps can be completed.
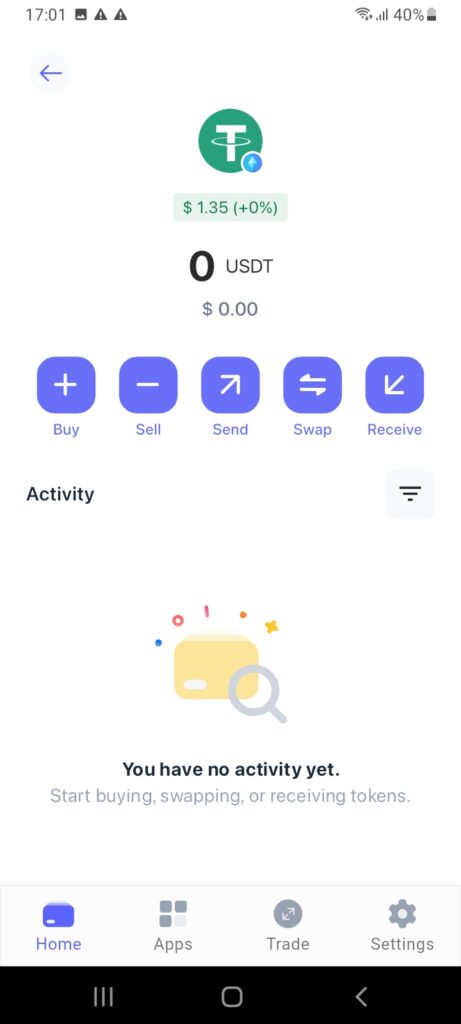
After that, you can instantly send, receive, and trade cryptocurrencies via decentralized exchanges. This can be done no matter where you’re located, assuming you’re carrying the respective smartphone. Best Wallet will also be launching a browser extension. This comes with the same security controls but on a desktop device. The extension will be accessible on popular browsers like Chrome.
Software wallets are also a must when connecting to decentralized applications (dApps). With Best Wallet, users can connect with the preferred dApp via WalletConnect. This can be done for over 60 blockchain ecosystems, from Solana and Ethereum to Base, Arbitrum, and Polygon.
Hardware Wallets
Hardware wallets are considered the safest way to store cryptocurrencies. They come as physical devices, with prices ranging from about $70 to hundreds of dollars. Hardware wallets store private keys within the device. Users must typically enter a PIN on the device when authorizing transactions.
This makes hardware wallets considerably less convenient than software wallets. For example, you won’t be able to send or trade cryptocurrencies unless the device is with you. Therefore, hardware wallets are aimed at passive investors storing large amounts.
That said, some crypto investors use software and hardware wallets simultaneously:
- The vast majority of cryptocurrencies will be held in a hardware wallet, with the balance kept in a software wallet.
- This ensures investors can seamlessly access the crypto markets at any time.
- In keeping most cryptocurrencies on a hardware device, only a small percentage of the balance is exposed to the internet.
- Funds can be transferred between both wallets quickly and securely.
Ultimately, Best Wallet is the best option for security-conscious investors who want frictionless access to the markets. On the security side, balances are protected by encrypted private keys, biometrics, and 2FA. Best Wallet is a self-custody solution, so users can send, receive, and trade the best cryptocurrencies without seeking approval.
Best Wallet users can also buy and sell cryptocurrencies with fiat currencies – no KYC documents are needed. What’s more, Best Wallet not only connects with Web 3.0 dApps, but it also comes with an in-built crypto launchpad.
This means users can safely invest in brand-new cryptocurrencies before they’re added to public exchanges.
References
- Device security guidance (National Cyber Security Centre)
- What is a man-in-the-middle (MITM) attack? (IBM)
- Crypto murder case in South Korea spurs tighter industry regulation (The Straits Times)
- Crypto’s biggest hacks and heists after $1.5 billion theft from Bybit (Reuters)
- You could be leaving your crypto wallet open to hackers—here’s how to protect it (CNBC)
Frequently asked questions
Best Wallet users enjoy a safe wallet experience, with key security features including biometrics and 2FA. Private keys are encrypted on the user’s device, ensuring complete control of the wallet funds.
Best Wallet users should activate biometrics (which replaces the PIN) and 2FA for the most secure setup. Users should also avoid clicking suspicious links, using the wallet on public WiFi, and sharing crypto wealth with other people.
As the safest Bitcoin wallet offering hot storage, Best Wallet users enjoy the perfect balance between security and convenience. Cold wallets are suitable for passive investors holding significant crypto balances.
Yes, besides activating non-mandatory features like 2FA and biometrics, Best Wallet users might consider using a dedicated smartphone for their wallet activities. That device can be left in airplane mode whenever the wallet isn’t being used, preventing remote hacking attempts.
Best Wallet users can back up their wallets by writing down the secret recovery phrase. This 12-word passphrase is shown when the wallet app is initially set up.